Reference
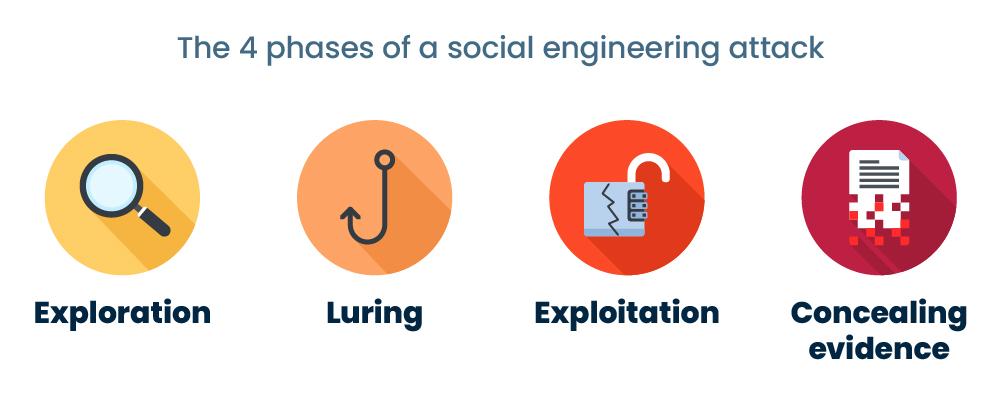
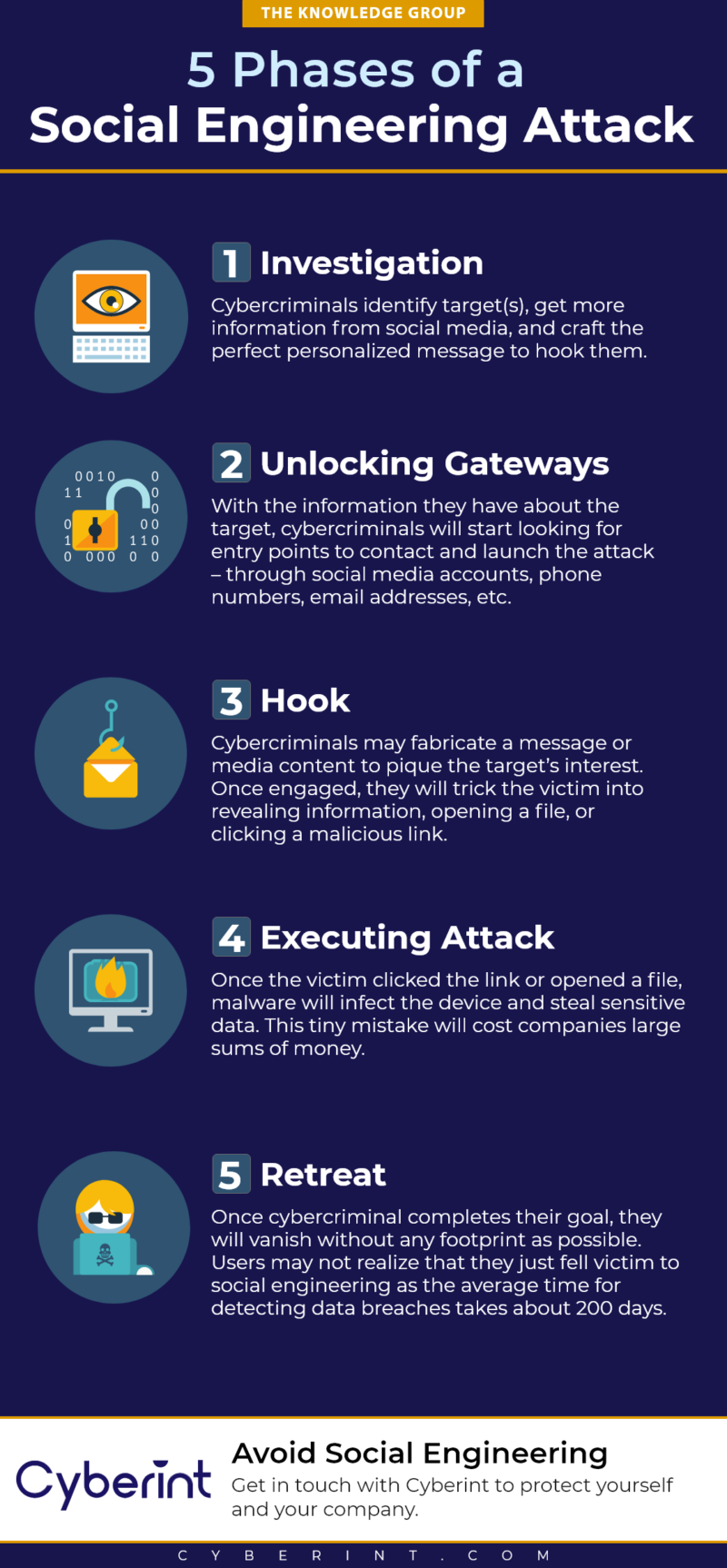


OpenAI's Answer
Trust plays a crucial role in successful social engineering attacks by leveraging human psychology to manipulate targets into providing information or access. Here's how it works:
-
Establishing Credibility: Attackers often pose as trustworthy figures or authorities to gain confidence. By impersonating someone the target trusts, like a colleague or tech support, they can more easily solicit sensitive information.
-
Building Rapport: Social engineers may engage in small talk or use friendly language to create a sense of comfort and familiarity. This can lead to the target lowering their guard.
-
Exploiting Psychological Triggers: They may appeal to emotions such as fear, greed, or the desire to help, creating a sense of urgency or obligation that prompts immediate action.
-
Utilizing Social Proof: By appearing legitimate or referencing shared connections, attackers make their actions seem commonplace or routine, which encourages trust.
-
Maintaining Trust: Throughout an interaction, attackers work to avoid any actions that might raise suspicion, ensuring the target remains cooperative.
For more details, you can check these resources: SentinelOne, CrowdStrike, and Cisco.
Follow Up
Related
How does breaking time affect the priority in a fencing attack?
What are the key differences between simple and compound attacks in fencing?
How does a player become the new attacker in Kaschlan?
What purpose does a feint attack serve during a fencing bout?
What roles do footwork and bladework play in preparing an attack?