Reference



Reference




OpenAI's Answer
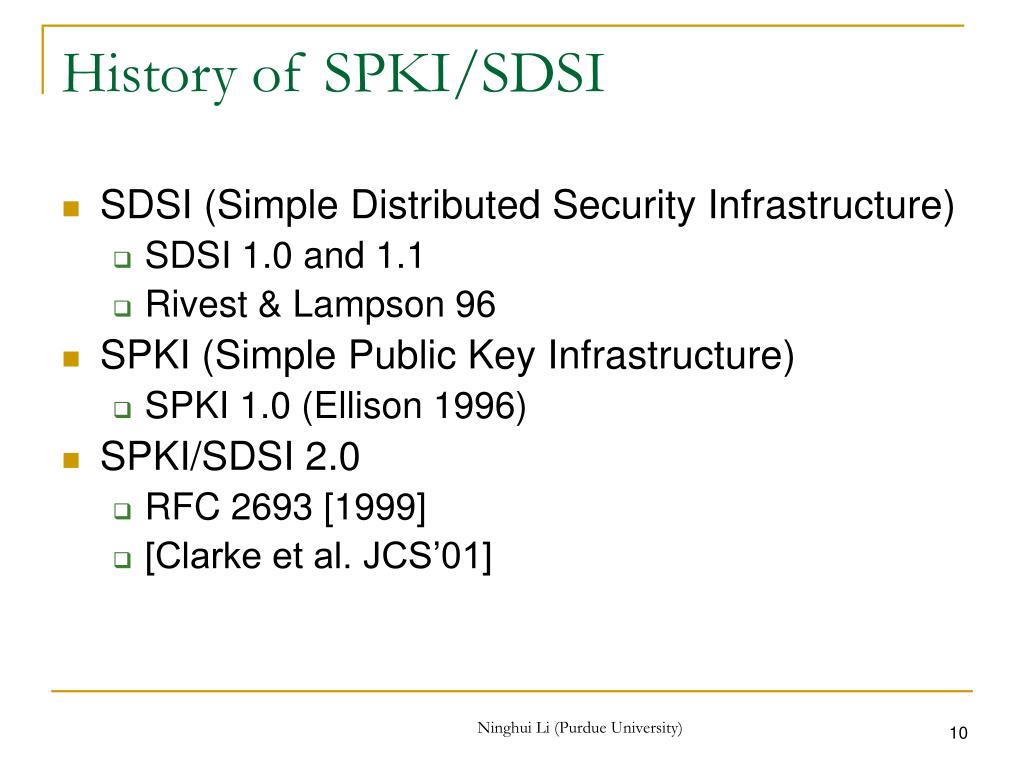
The original Simple Public Key Infrastructure (SPKI) and Simple Distributed Security Infrastructure (SDSI) had distinct approaches to authorization:
-
SPKI Authorization: SPKI identified principals primarily by their public keys and allowed for binding authorizations directly to these keys. Furthermore, SPKI supported the delegation of authorization from one key to another. This means that SPKI centered on assigning permissions at the level of public keys, where public keys represented entities or individuals. The underlying mechanism employed was an attribute:value pairing system, akin to RFC 822 headers, which facilitated this binding and delegation process.
-
SDSI Authorization: SDSI focused on binding local names (of individuals or groups) to public keys or other names and carried authorizations within Access Control Lists (ACLs). Rather than authorizing actions directly through keys, SDSI incorporated a naming system that worked alongside the authorization, meaning that permissions were managed more through these local names linked to public keys. In SDSI, it was more about defining who had access through ACLs associated with these names, which were locally defined.
For a deeper understanding of these mechanisms and their differences, you can refer to Wikipedia's Simple Public Key Infrastructure page.
Additionally, here are some images related to the SPKI and SDSI authorization models:


Follow Up
Related
Which authors received both the NIN Award and the Ivo Andrić Award?
Which books were authored or co-authored by John L. Jambor?
Who are some notable figures from West Bengal in literature, science, and politics?
Which author won the Governor General's Award for English-language fiction multiple times?